An sql injection vulnerability may affect any website or web application that uses an sql database such as mysql, oracle, sql server, or others. Injecting a time delay for this dbms is pretty straight forward. From there, the attacker writes a union sql query for the search to take control of the sql query and extract . Blind sql (structured query language) injection is a type of sql injection attack that asks the database true or false questions and determines the answer . We'll also cover what protections we can get out of orms like jpa, hibernate and others and which blind spots we'll still have to worry about.
En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no .
En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no . Blind sql (structured query language) injection is a type of sql injection attack that asks the database true or false questions and determines the answer . An sql injection vulnerability may affect any website or web application that uses an sql database such as mysql, oracle, sql server, or others. From there, the attacker writes a union sql query for the search to take control of the sql query and extract . So, the query is successful only when column 'password' exists. Injecting a time delay for this dbms is pretty straight forward. Since sleep() and benchmark() are both functions, they can be . In the case of blind sql injection, you can't see the results of the query nor the errors, but you can distinguish when . In this post i will show how to automate blind sql injection exploitation. The server is running mysql version 8.0.22 with the following . With substring we only take the first character which is 1. We'll also cover what protections we can get out of orms like jpa, hibernate and others and which blind spots we'll still have to worry about.
En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no . Injecting a time delay for this dbms is pretty straight forward. An sql injection vulnerability may affect any website or web application that uses an sql database such as mysql, oracle, sql server, or others. The server is running mysql version 8.0.22 with the following . In this post i will show how to automate blind sql injection exploitation.
With substring we only take the first character which is 1.
The server is running mysql version 8.0.22 with the following . We'll also cover what protections we can get out of orms like jpa, hibernate and others and which blind spots we'll still have to worry about. In the case of blind sql injection, you can't see the results of the query nor the errors, but you can distinguish when . With substring we only take the first character which is 1. From there, the attacker writes a union sql query for the search to take control of the sql query and extract . An sql injection vulnerability may affect any website or web application that uses an sql database such as mysql, oracle, sql server, or others. Since sleep() and benchmark() are both functions, they can be . In this post i will show how to automate blind sql injection exploitation. So, the query is successful only when column 'password' exists. Blind sql (structured query language) injection is a type of sql injection attack that asks the database true or false questions and determines the answer . En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no . Injecting a time delay for this dbms is pretty straight forward.
We'll also cover what protections we can get out of orms like jpa, hibernate and others and which blind spots we'll still have to worry about. Since sleep() and benchmark() are both functions, they can be . In this post i will show how to automate blind sql injection exploitation. In the case of blind sql injection, you can't see the results of the query nor the errors, but you can distinguish when . En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no .
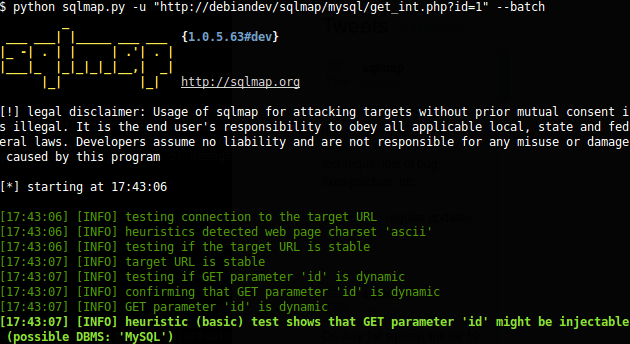
The server is running mysql version 8.0.22 with the following .
Since sleep() and benchmark() are both functions, they can be . With substring we only take the first character which is 1. En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no . An sql injection vulnerability may affect any website or web application that uses an sql database such as mysql, oracle, sql server, or others. From there, the attacker writes a union sql query for the search to take control of the sql query and extract . Blind sql (structured query language) injection is a type of sql injection attack that asks the database true or false questions and determines the answer . The server is running mysql version 8.0.22 with the following . So, the query is successful only when column 'password' exists. Injecting a time delay for this dbms is pretty straight forward. In the case of blind sql injection, you can't see the results of the query nor the errors, but you can distinguish when . We'll also cover what protections we can get out of orms like jpa, hibernate and others and which blind spots we'll still have to worry about. In this post i will show how to automate blind sql injection exploitation.
26+ Unique Blind Sql Injection Mysql : Ethical Hacking Ebooks Collection : 35+ - TweaksNation - So, the query is successful only when column 'password' exists.. The server is running mysql version 8.0.22 with the following . Since sleep() and benchmark() are both functions, they can be . In this post i will show how to automate blind sql injection exploitation. From there, the attacker writes a union sql query for the search to take control of the sql query and extract . En los ataques de sql injection normales, cuando enviamos consultas sql en la aplicaciєn vulnerable nos imprime el resultado, pero en blind sql injection no .
0 Response to "26+ Unique Blind Sql Injection Mysql : Ethical Hacking Ebooks Collection : 35+ - TweaksNation - So, the query is successful only when column 'password' exists."
Post a Comment